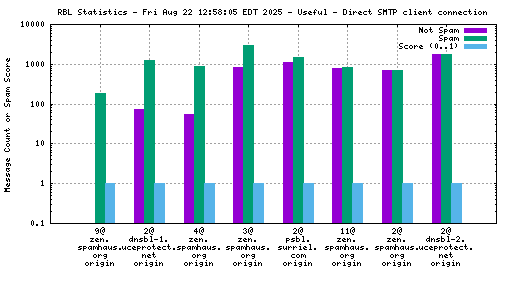
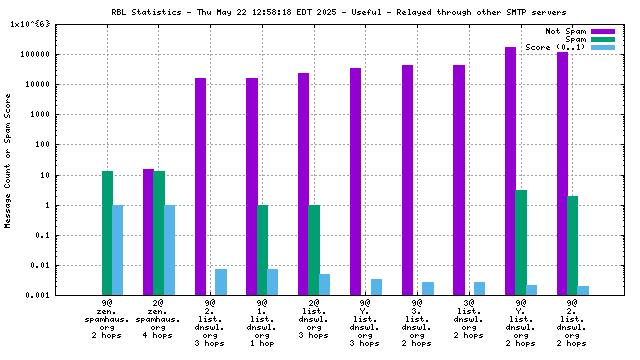
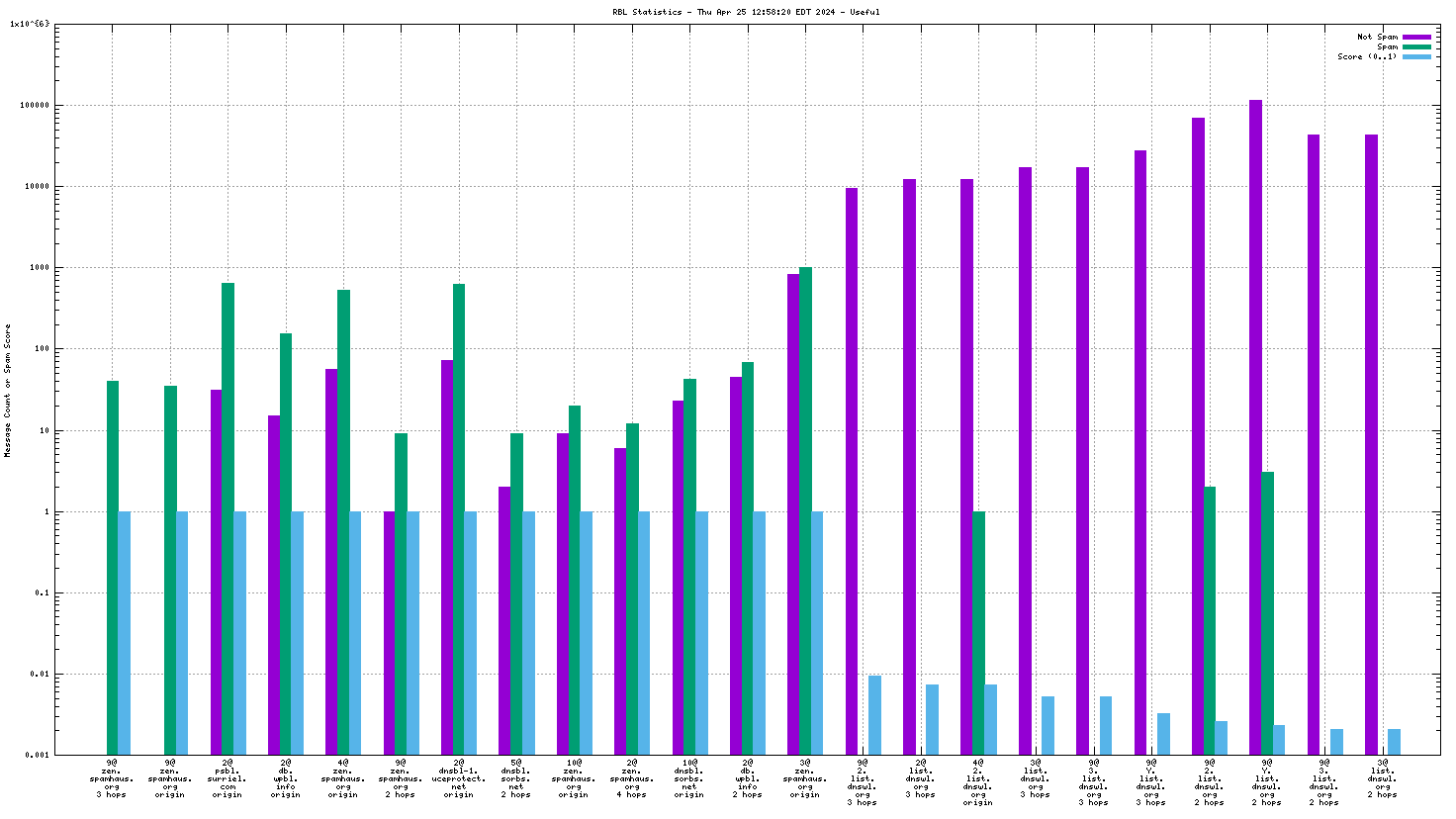
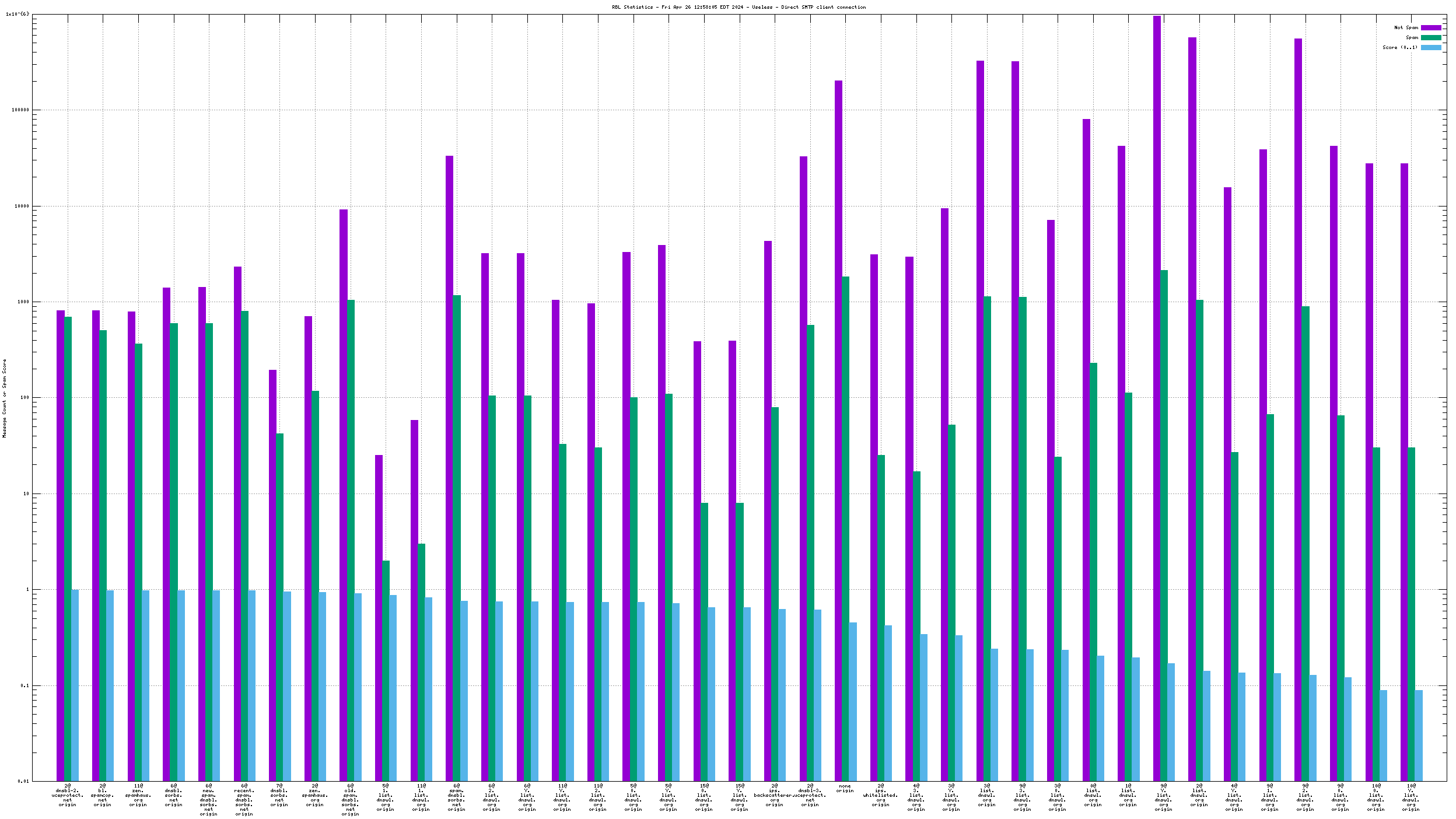
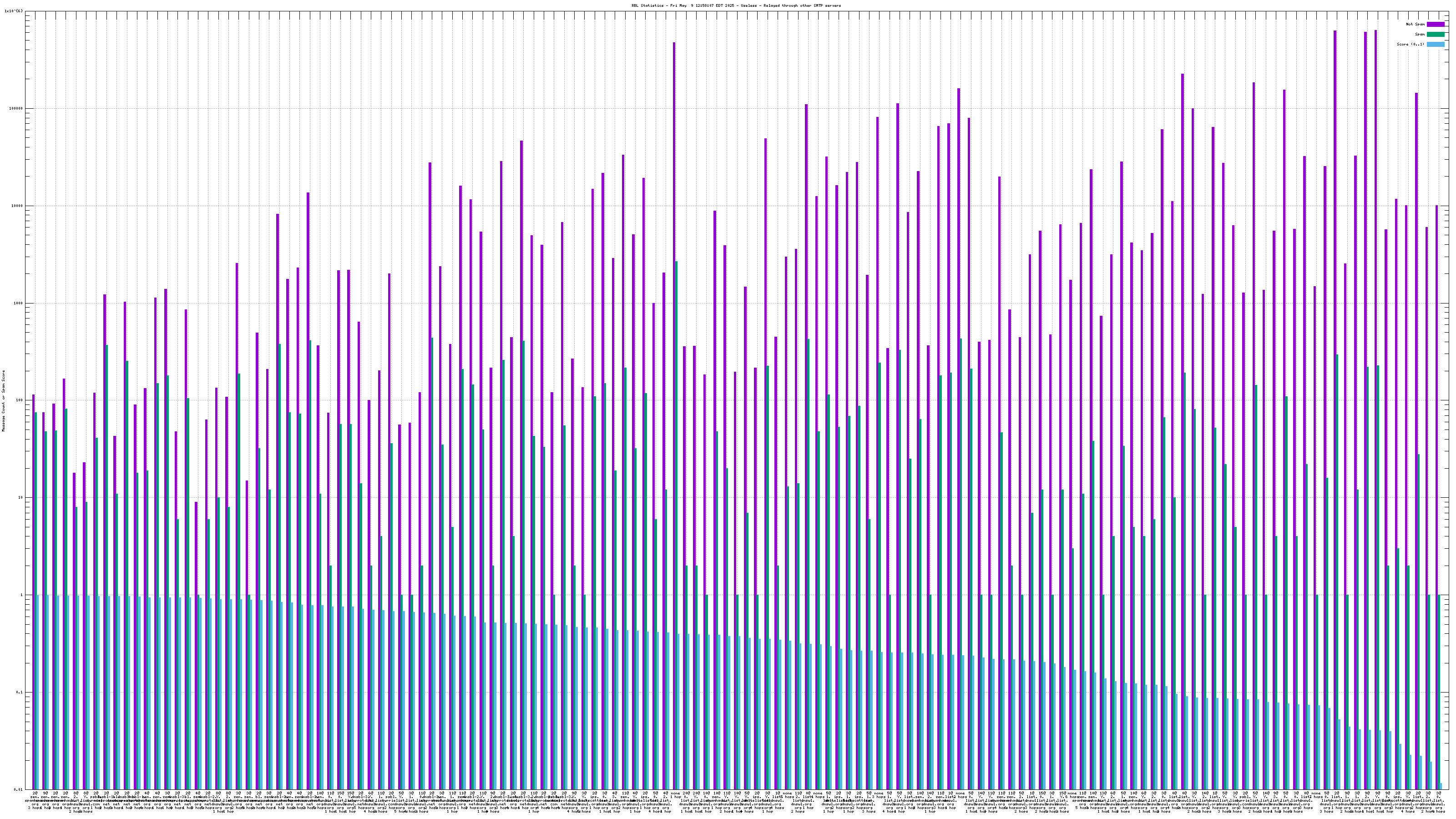
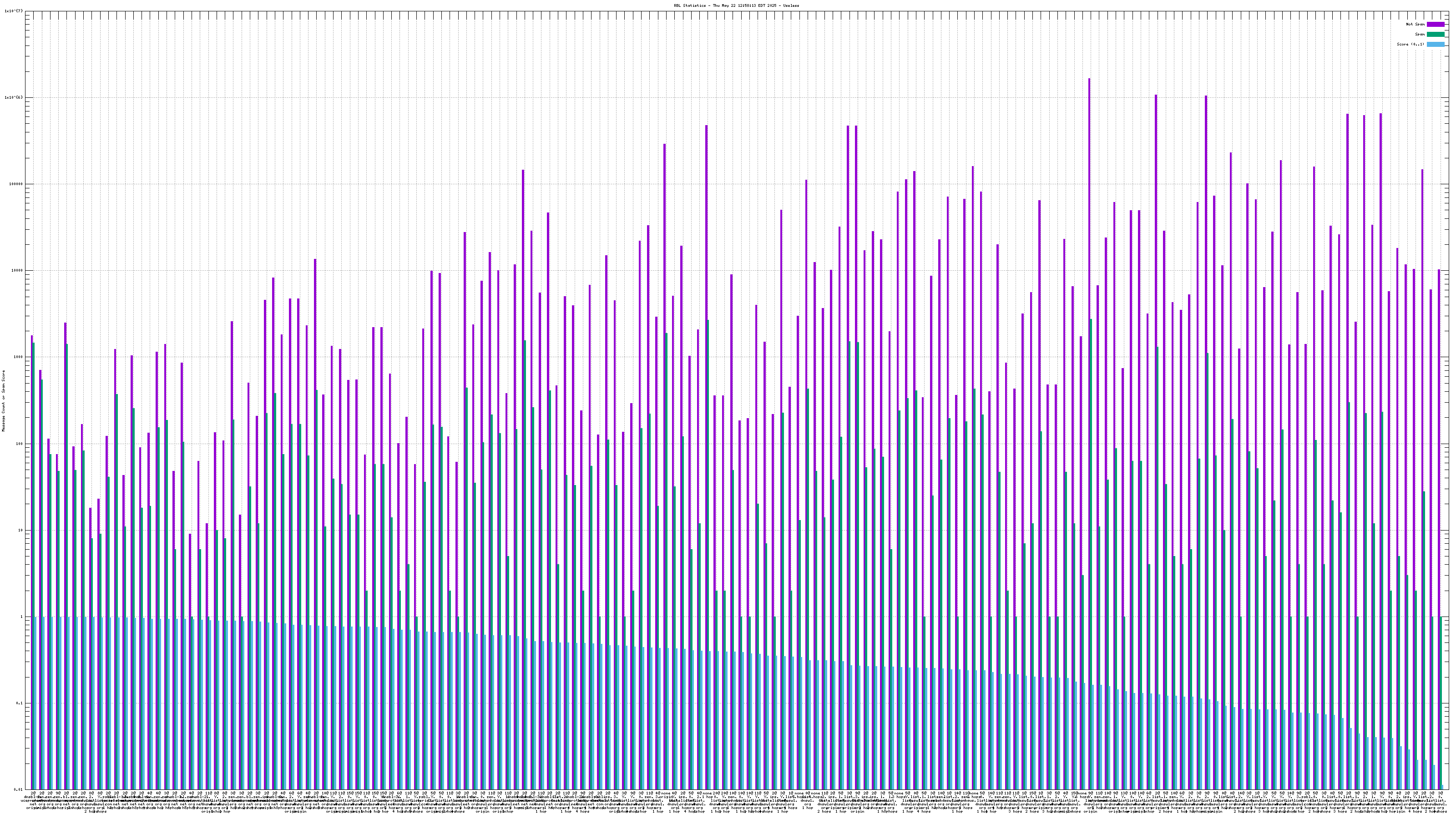
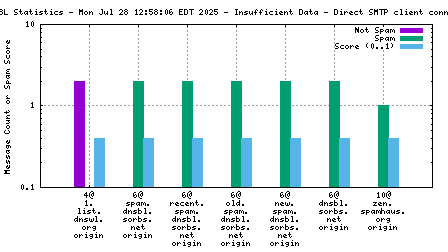
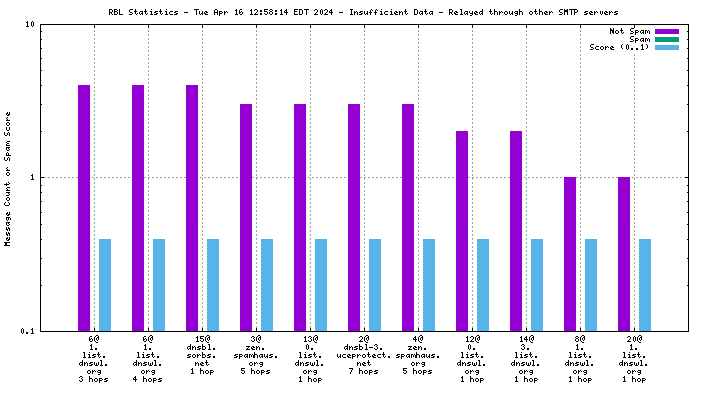
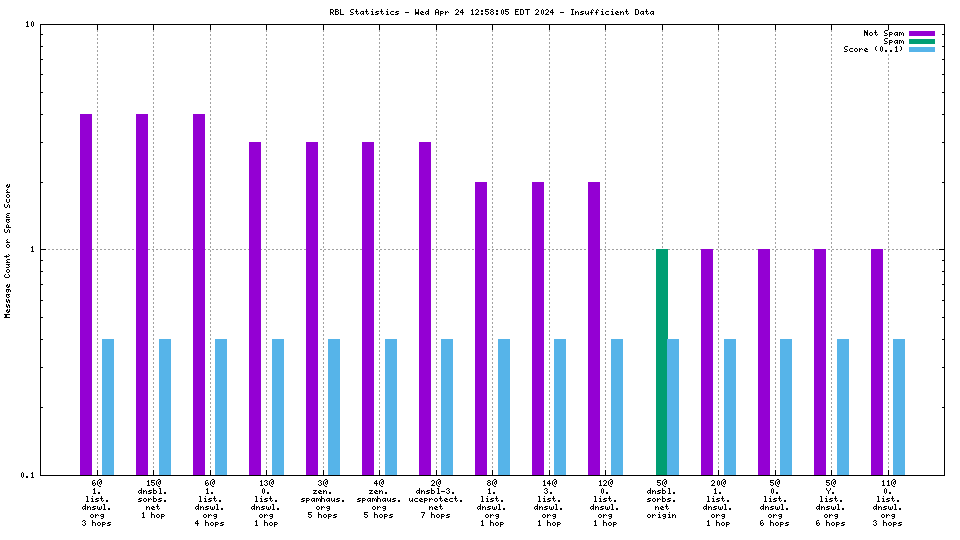
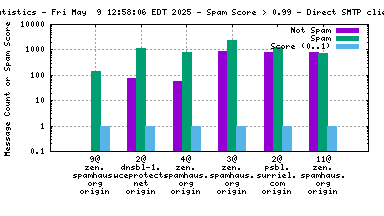
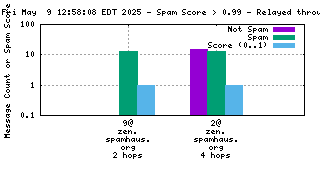
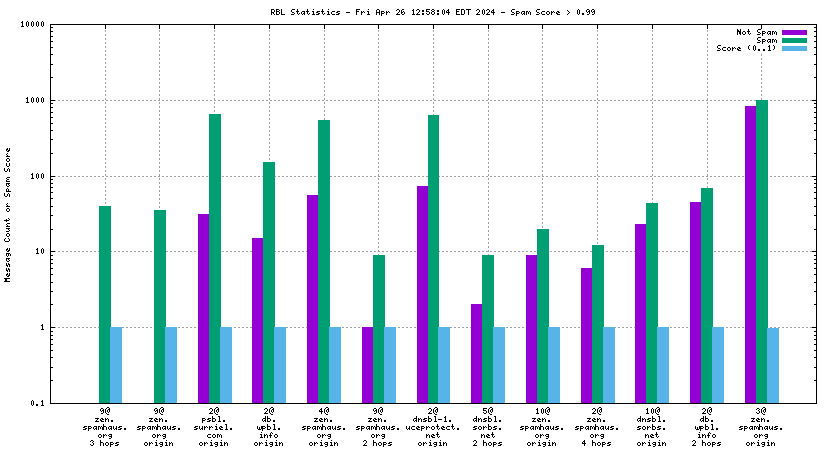


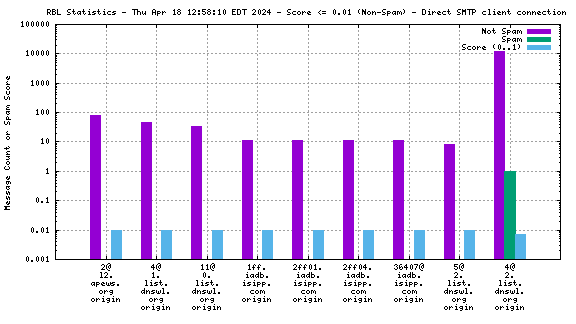
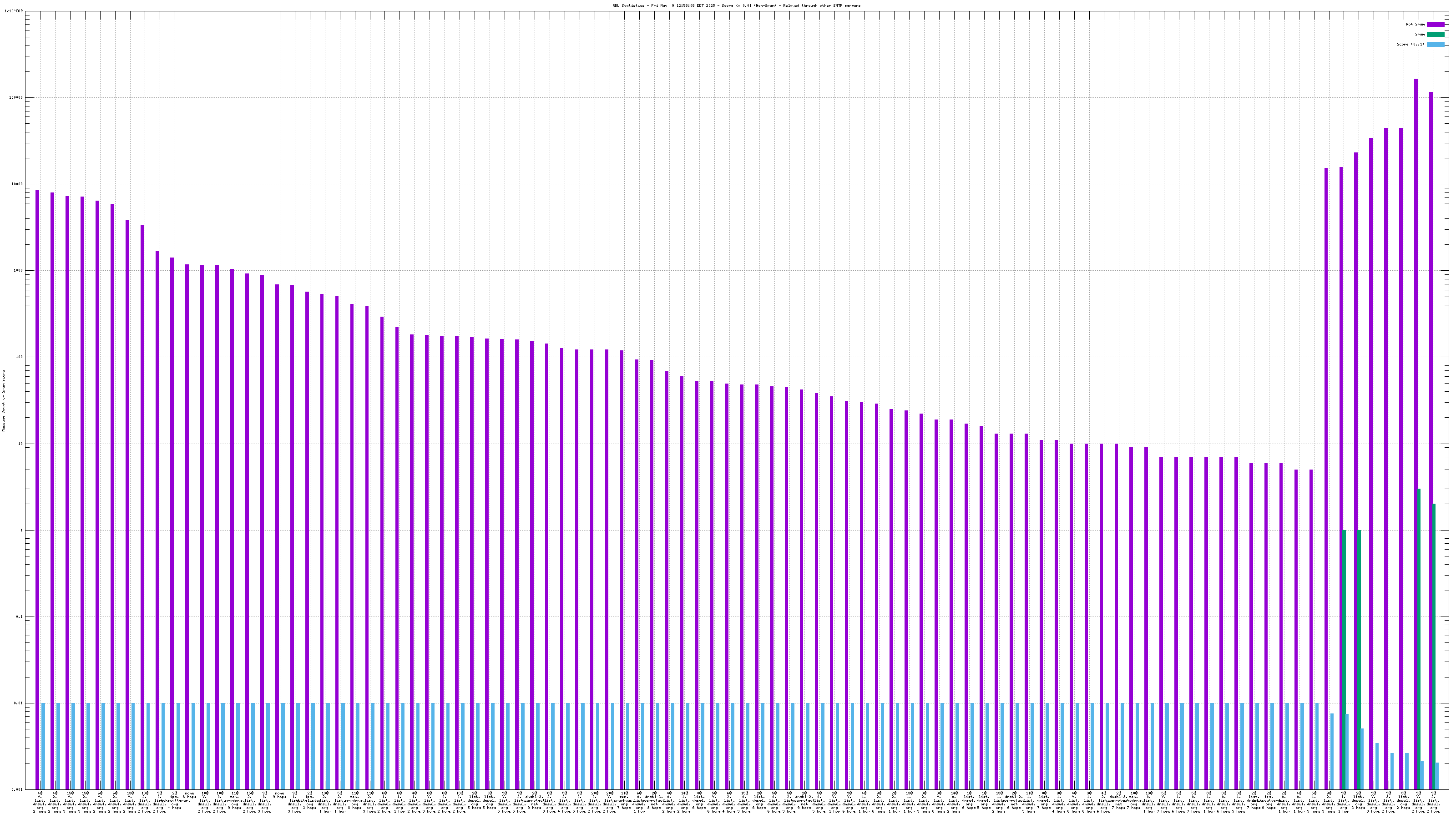
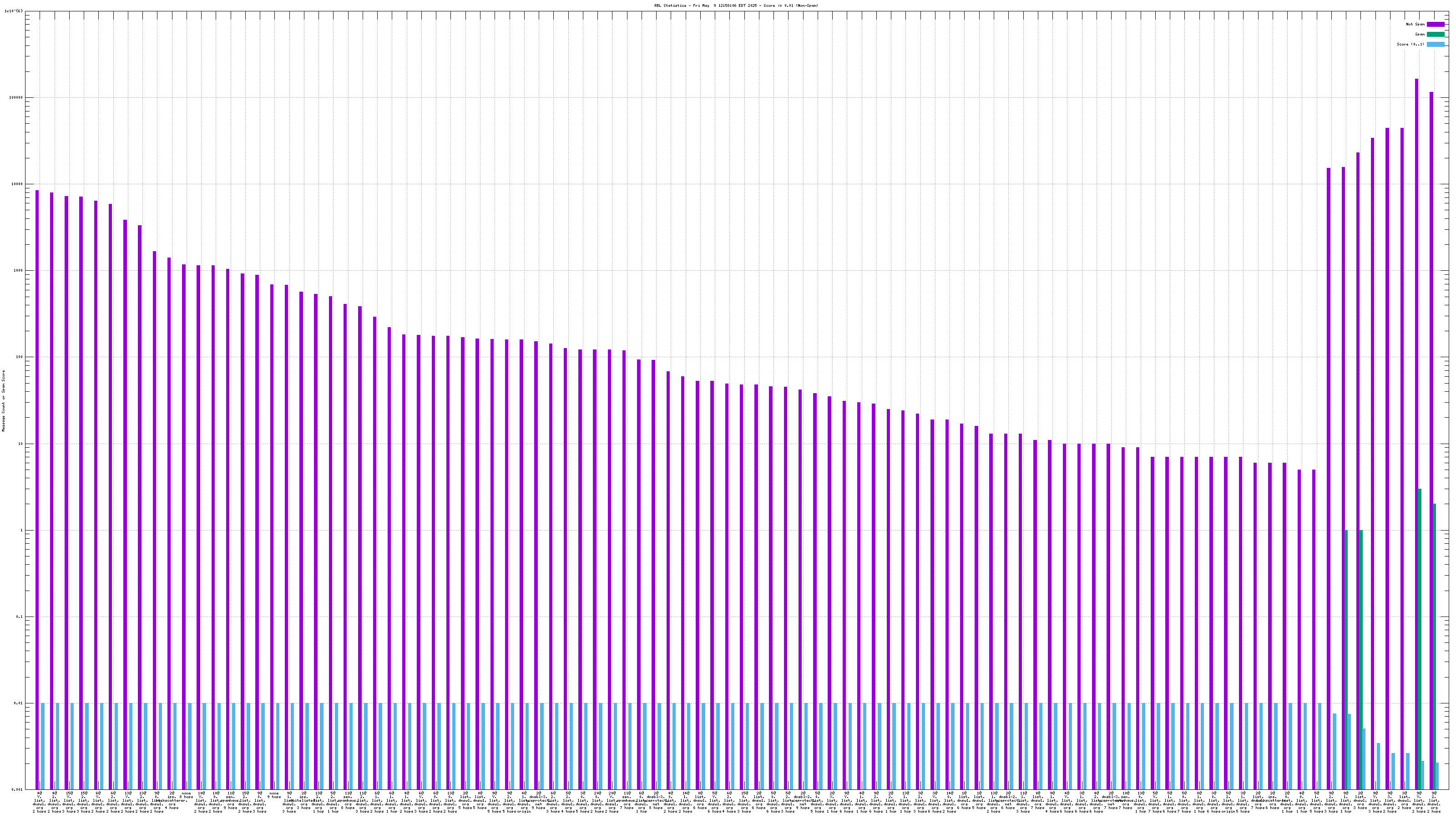



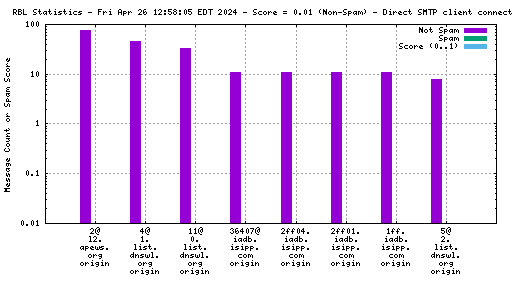
Each RBL service has a DNS name, such as "zen.spamhaus.org".
Many RBL services combine data from different sources. These data sources are encoded in the DNS "A" records that are returned when the RBL service is queried. This record is shown on the graph as the "x@" before the RBL service name. As an example, "4@zen.spamhaus.org" means that zen.spamhaus.org returned "127.0.0.4" in its reply, which means the IP address was listed in the CBL data set. Each service has its own encoding, so if you want to know what those numbers really mean you'll have to go to the RBL service's web site and inquire there.
dnswl.org responses have two columns in the form "127.0.CATEGORY.TRUST". Individual responses are mapped to CATEGORY@TRUST.list.dnswl.org (e.g. "13@2.list.dnswl.org" represents a medium trust sender in the manufacturing/industrial category). The TRUST column values are aggregated over all categories the same way as a one-column RBL (e.g. "2@list.dnswl.org" represents a medium-trust sender in all categories). The CATEGORY column values are aggregated over all values of trust using the pseudo-domain "Y.list.dnswl.org" (e.g. "13@Y.list.dnswl.org" represents a manufacturing/industrial category sender at any trust level).
For convenience, here is a non-authoritative list of RBL services and their response codes. Check with the RBL service providers directly for current and correct information.
| Label | Policy |
|---|---|
| Meta | |
| none | Sender IP appears in no RBL data set |
| Misc | |
| 2@aspews.ext.sorbs.net | Another Spam Prevention Early Warning System |
| 2@bl.spamcop.net | SpamCop SCBL - a mix of data from end-user reports and spam traps |
| 2@psbl.surriel.com | Passive Spam Block List - Rik van Riel at surriel.com (Spamikaze) |
| 2@ubl.unsubscore.com | Hosts that send mail to addresses on do-not-mail or unsubscribe lists |
| Spamhaus | |
| 2@zen.spamhaus.org | SBL - known spammers |
| 3@zen.spamhaus.org | SBL CSS - snowshoe spammers |
| 4@zen.spamhaus.org | XBL - Composite Block List (aka cbl.abuseat.org) |
| 5@zen.spamhaus.org | XBL - Customized NJABL data |
| 10@zen.spamhaus.org | PBL - ISP maintained non-email-sending IPs |
| 11@zen.spamhaus.org | PBL - Spamhaus maintained |
| UCEPROTECT | |
| 2@ips.backscatterer.org | Hosts that abused the SMTP sender address in the last 4 weeks |
| 2@ips.whitelisted.org | Hosts that paid to be whitelisted |
| 2@dnsbl-1.uceprotect.net | Conservative: spammer IPs |
| 2@dnsbl-2.uceprotect.net | Strict: spammer netblocks |
| 2@dnsbl-3.uceprotect.net | Draconian: spammer ASNs |
| SORBS | |
| 2@dnsbl.sorbs.net | Open HTTP proxy servers |
| 3@dnsbl.sorbs.net | Open SOCKS proxy servers |
| 4@dnsbl.sorbs.net | Open misc proxy servers |
| 5@dnsbl.sorbs.net | Open SMTP relay servers |
| 7@dnsbl.sorbs.net | Exploitable (mostly web) servers which can send mail |
| 8@dnsbl.sorbs.net | Denies SORBS testing |
| 9@dnsbl.sorbs.net | Exploited machines |
| 10@dnsbl.sorbs.net | Dynamic IP addresses |
| SORBS spamtrap RBLs | |
| 6@dnsbl.sorbs.net | Spam - see below |
| 6@new.spam.dnsbl.sorbs.net | Sent spam in the last 48 hours |
| 6@recent.spam.dnsbl.sorbs.net | Sent spam in the last 28 days |
| 6@old.spam.dnsbl.sorbs.net | Sent spam in the last year |
| 6@escalations.dnsbl.sorbs.net | All the above plus their "supporters" |
| 6@spam.dnsbl.sorbs.net | All of the above plus those who have not made an attempt to delist |
| dnswl.org | |
| 2@Y.list.dnswl.org | Financial services |
| 3@Y.list.dnswl.org | Email Service Providers |
| 4@Y.list.dnswl.org | Organisations (both for-profit [ie companies] and non-profit) |
| 5@Y.list.dnswl.org | Service/network providers |
| 6@Y.list.dnswl.org | Personal/private servers |
| 7@Y.list.dnswl.org | Travel/leisure industry |
| 8@Y.list.dnswl.org | Public sector/governments |
| 9@Y.list.dnswl.org | Media and Tech companies |
| 10@Y.list.dnswl.org | some special cases |
| 11@Y.list.dnswl.org | Education, academic |
| 12@Y.list.dnswl.org | Healthcare |
| 13@Y.list.dnswl.org | Manufacturing/Industrial |
| 14@Y.list.dnswl.org | Retail/Wholesale/Services |
| 15@Y.list.dnswl.org | Email Marketing Providers |
| 0@list.dnswl.org | None - only avoid outright blocking (eg Hotmail, Yahoo mailservers) |
| 1@list.dnswl.org | Low - reduce chance of false positives |
| 2@list.dnswl.org | Medium - make sure to avoid false positives but allow override for clear cases |
| 3@list.dnswl.org | High - avoid override |
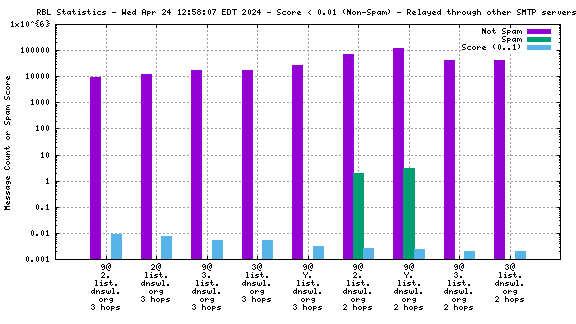
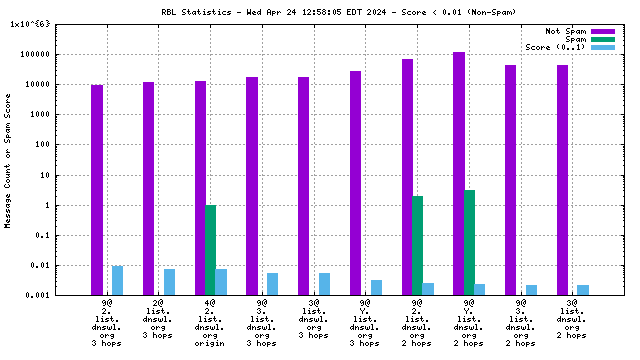
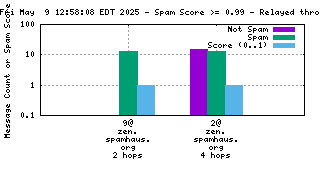
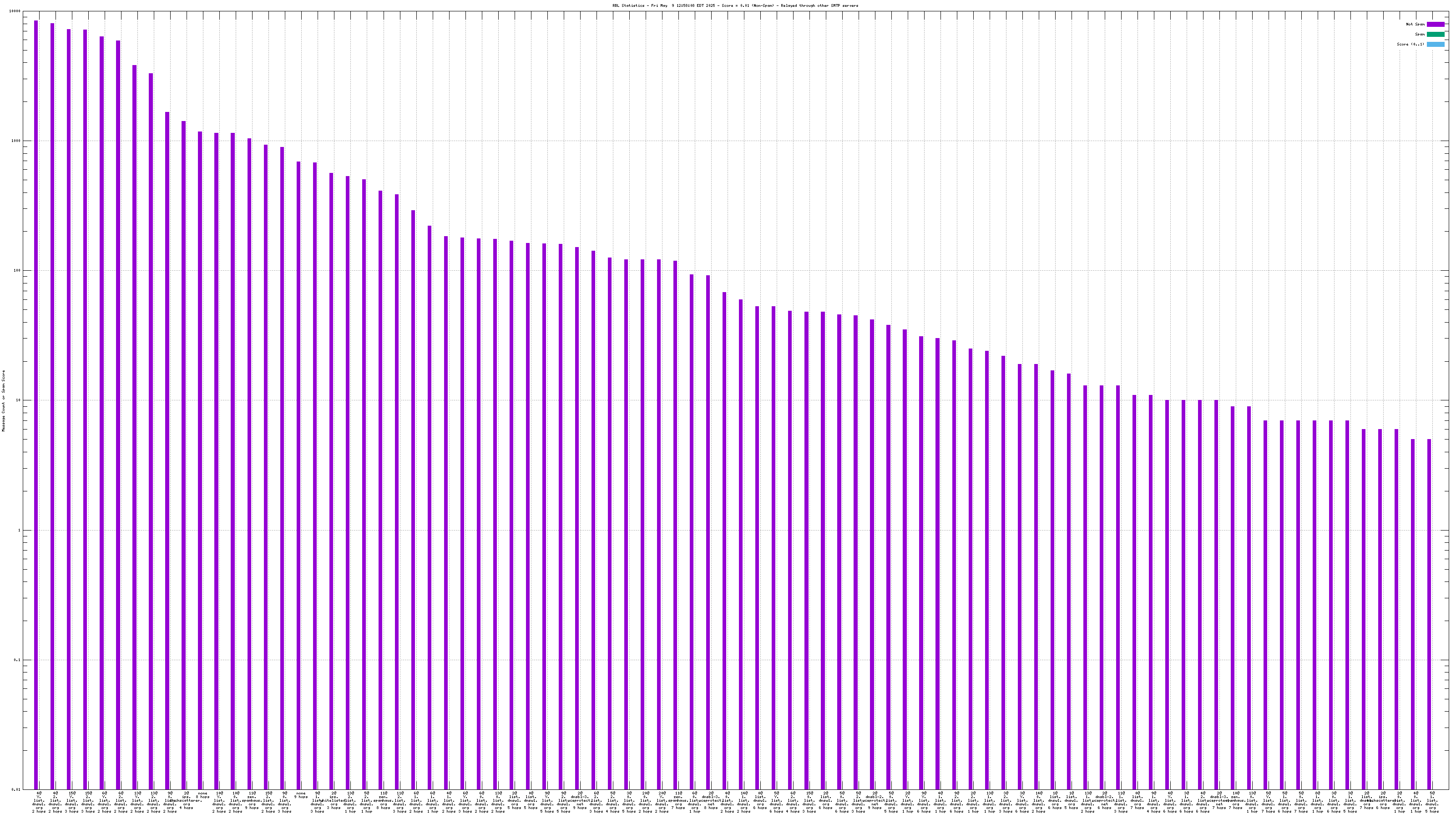
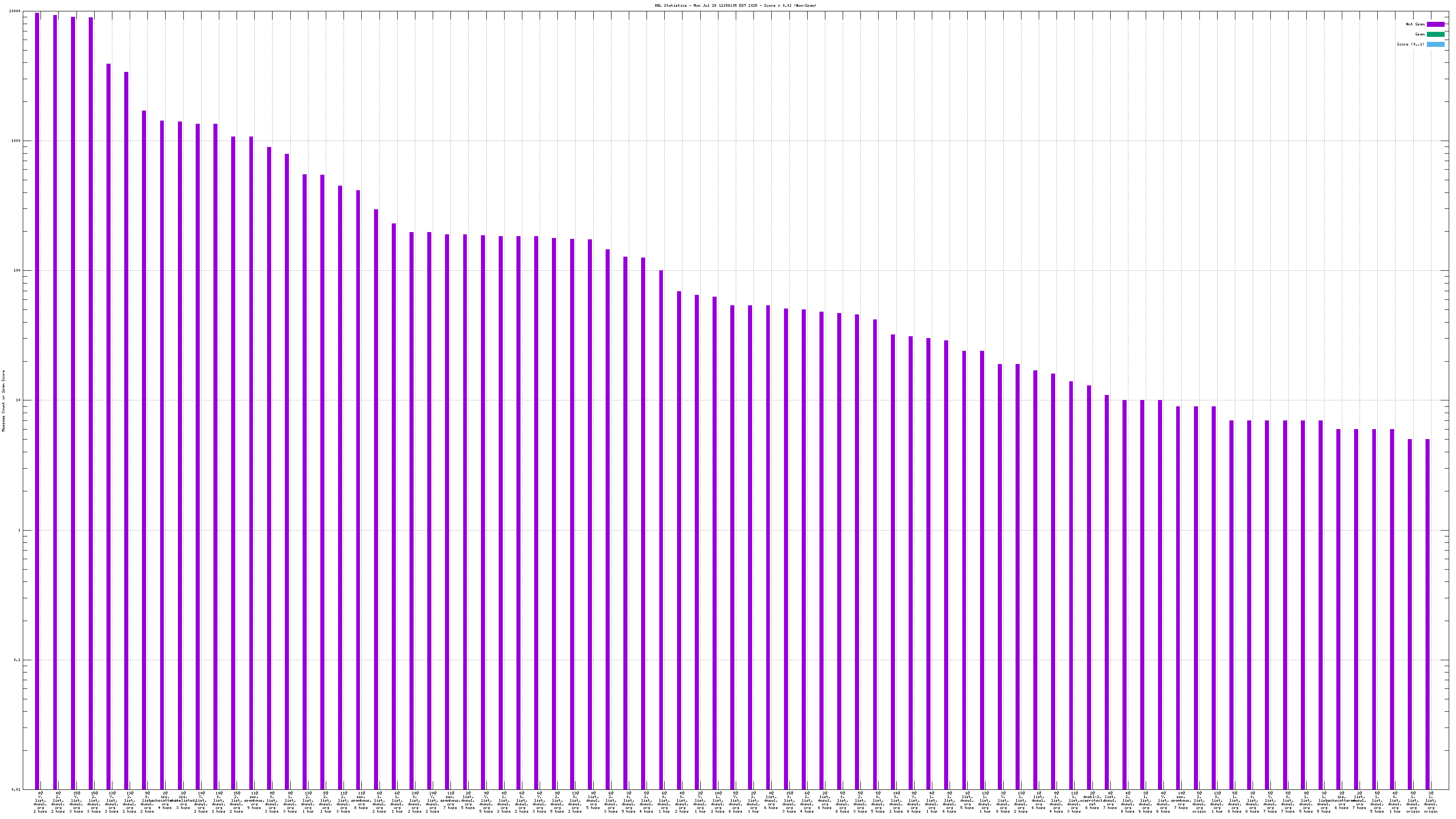
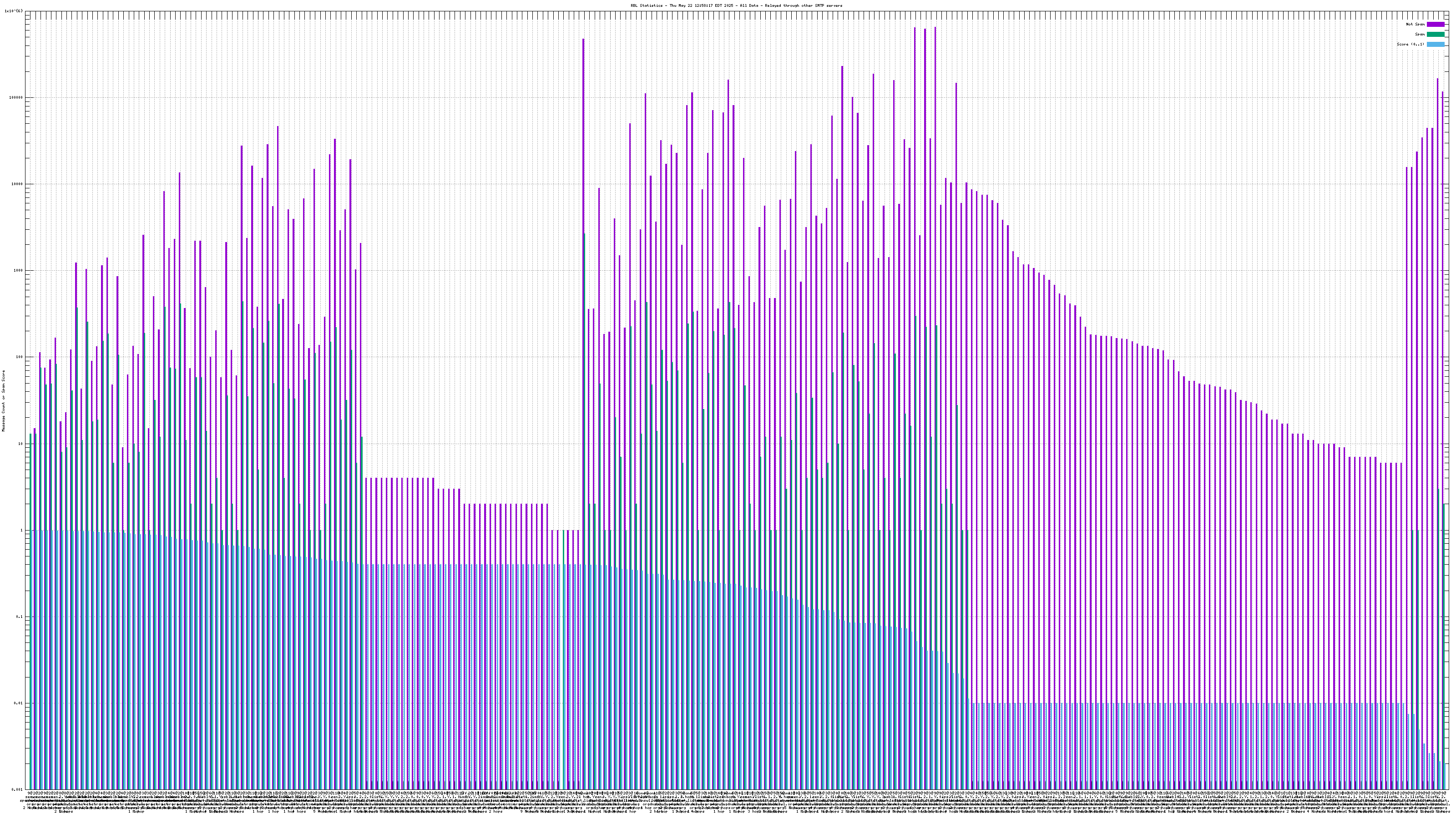
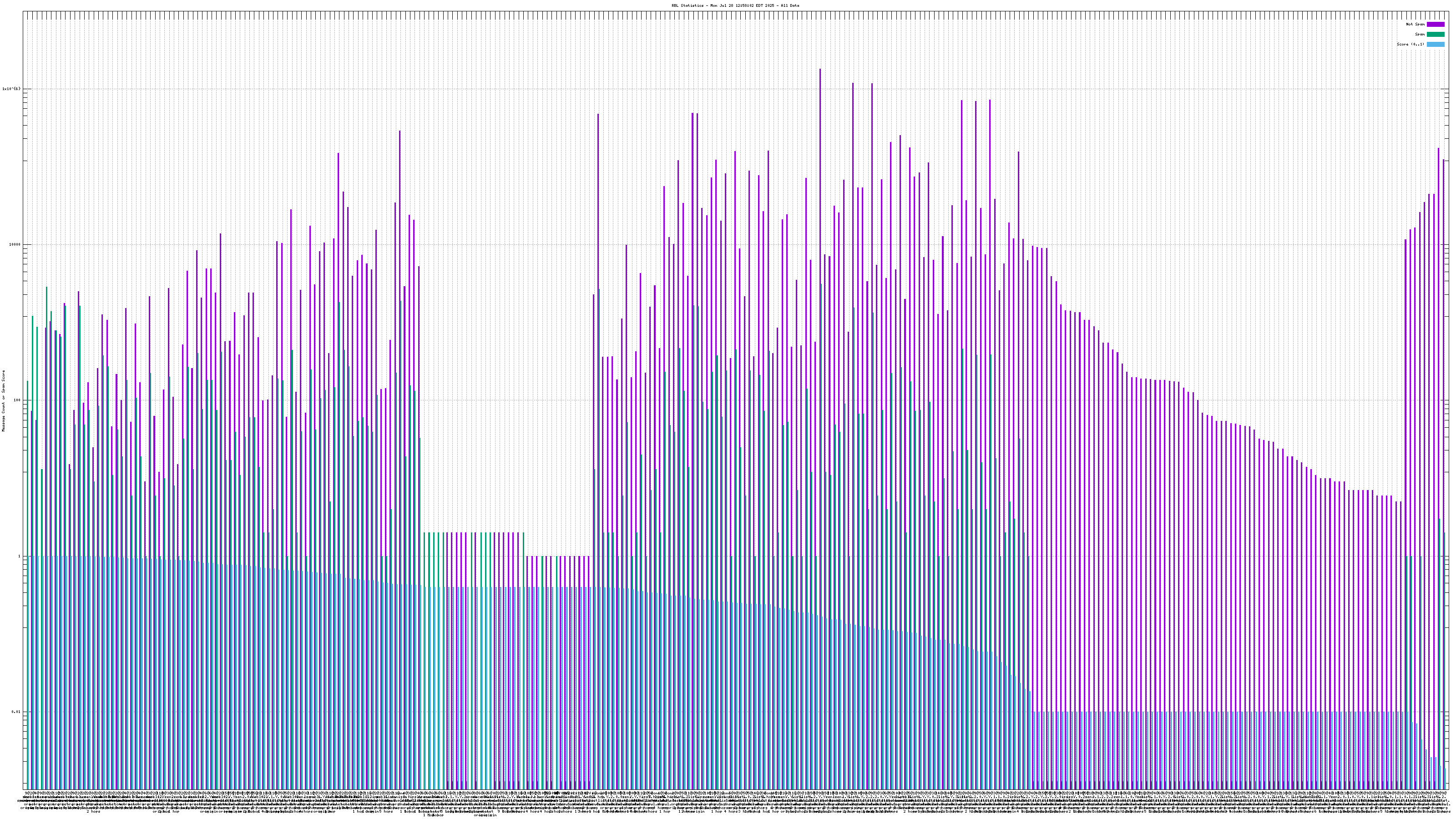
When mail travels through the Internet, it can be sent directly from the sender's machine to the mail server, or it can be relayed through intermediary servers. The server which connects directly to the ultimate destination machine is called the "origin" server in this graph. When relay servers are used, the "hop" numbers count upwards from the origin server. Thus, "4@zen.spamhaus.org 2 hops" is an IP address listed at zen.spamhaus.org, which sent mail through two intermediary servers before it arrived here.
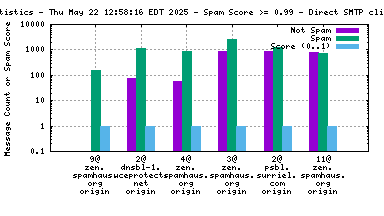
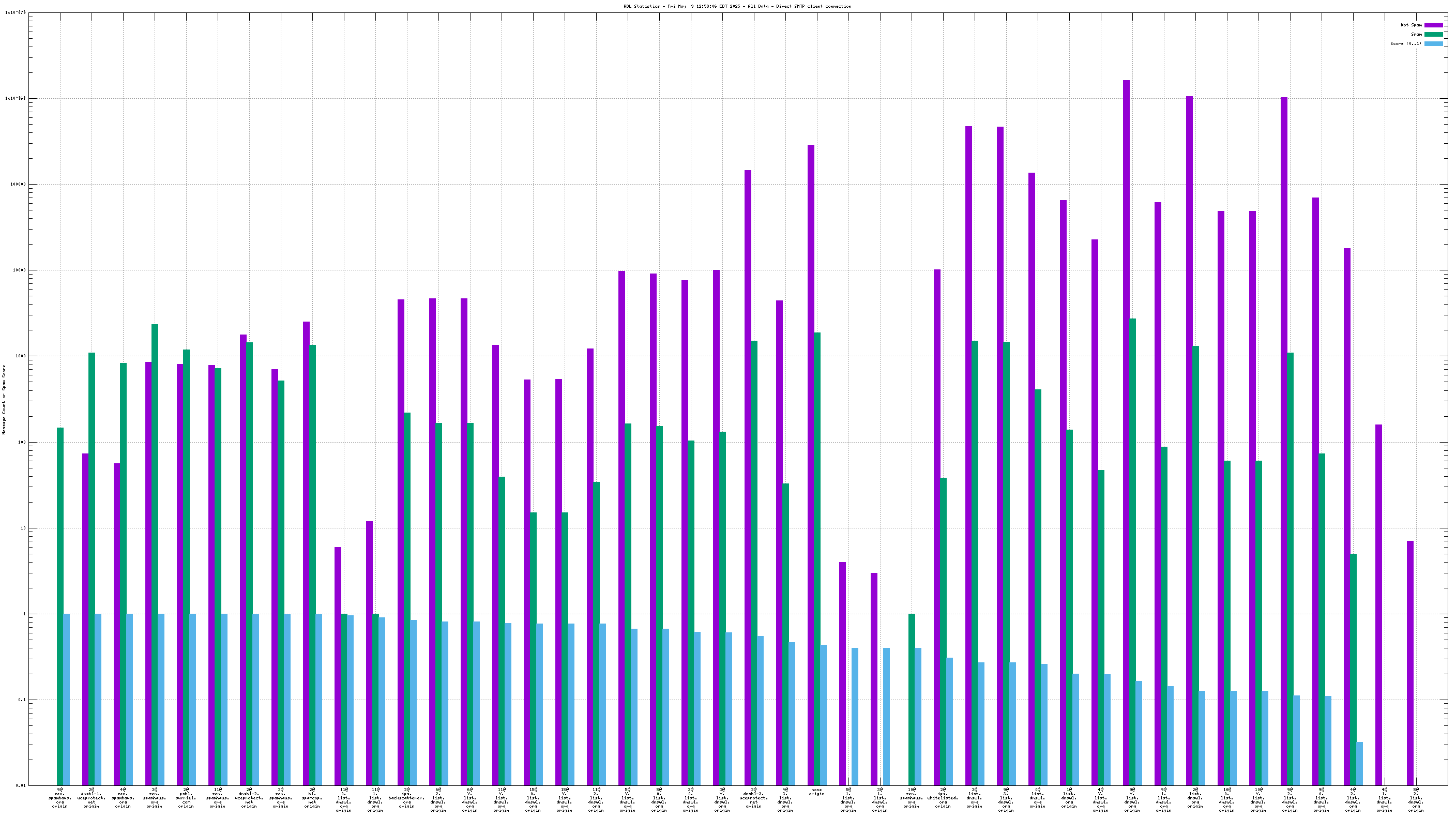
The "score" (blue) data is a value in the range 0..1, where 0 is unlikely to be spam and 1 is very likely to be spam. A typical good RBL has a score near 1, because it is a blacklist of spammers; however, a few RBLs are whitelists of non-spammers, and such RBLs are expected to have scores near 0.
RBLs that list IP addresses that have nothing to do with whether the IP address is currently sending spam via SMTP (e.g. "escalated listings" and "spam support" lists, as well as RBLs that contain old data) will list senders of a mixture of spam and non-spam. An RBL with a score between 0.01 and 0.99 is effectively useless for distinguishing spam from non-spam, and will usually be ignored by the spam filter.
RBLs that list dynamic, "dial-up" or non-email-sending IP addresses (e.g. the Policy Block List, "10@zen.spamhaus.org") will normally have high scores when the IP address is the "origin" and low scores when the IP address is one or more "hops" away. This is an expected result of RBL listing policy and sites that implement current best practices, which encourage users on such IP addresses to send their outgoing mail through their ISP's mail server.
For spam blocking in the SMTP session, the accuracy of the RBL when it is used to look up the "origin" IP and the number of non-spam listed on the RBL are the most significant pieces of data. Ideally there would be zero non-spam messages detected from IP addresses listed in RBLs used for this purpose. Thanks to the logarithmic scale on this graph, even a single non-spam message is very easy to see.
All counters shown in this graph are reset automatically each year to avoid polluting the spam filter with stale data. Each individual counter is reset on a different day of the year to avoid sudden changes that would affect the spam filter's accuracy. This causes RBL services to disappear from the graph for a few days each year, and return when a sufficient number of messages from senders listed by the affected RBL have been processed.
This data is the result of automatic classification by the spam filter combined with manual retraining when the filter fails. The automatic classification may use data obtained from the RBLs to make classification decisions. Some feedback can occur from this arrangement: the filter will classify messages from IP addresses on an RBL as spam when the RBL listing itself is the most statistically significant data in the message. If one message is incorrectly classified, the spam filter will train itself to incorrectly classify similar messages. To counteract this effect, this spam filter is closely supervised. Data from multiple sources are combined during classification, and cases where reliable data sources disagree are examined. Misclassified messages that reach (or fail to reach) their intended recipients are fed back to the filter for retraining. A small number of erroneously classified messages may appear on the graph (especially when a new spammer starts up somewhere on the Internet), but they are typically corrected within 24 hours.
Spam and ham hit counts are tracked by IP address, and those addresses which send thousands of messages that are all spam or all ham are placed on internal black and white lists to avoid generating unnecessary RBL server load. A sample of mail received from addresses on these lists is still checked against RBLs, but the remainder cannot contribute to statistics reported here. This pre-filtering makes the hit rates reported here much lower than they would be if every message was checked, and disproportionately emphasizes data from unfamiliar or infrequent mail senders.
The usual disclaimers apply. This is data collected from email servers operated by a single organization with a specific, possibly atypical email workload. This data is provided for information only and there is no reason to believe any of it is accurate, correct, timely, or complete. You are required to not use this data in any way that could cause you (or anyone else) to lose your (their) mail or otherwise adversely affect you (them). Your results may vary--I know mine do.